Encryption converts unrecognizable data into recognizable data. – Encryption converts unrecognizable data into recognizable data, a process that plays a crucial role in protecting sensitive information in today’s digital world. This comprehensive guide delves into the intricacies of encryption, exploring its methods, applications, and ethical considerations.
Encryption safeguards data by transforming it into an unreadable format, rendering it inaccessible to unauthorized individuals. This transformation process involves the use of encryption algorithms and keys, ensuring that only authorized parties can decrypt and access the data.
1. Encryption Overview
Encryption is a vital data protection measure that safeguards sensitive information from unauthorized access and exploitation. It involves transforming data into an unreadable format, making it inaccessible to those without the necessary decryption key.
Encryption finds widespread applications in various sectors, including:
- Secure communication (e.g., email, instant messaging)
- Data storage (e.g., databases, cloud storage)
- Financial transactions (e.g., online banking, credit card payments)
Encryption provides numerous benefits, including:
- Confidentiality: Ensures that only authorized parties can access data.
- Integrity: Prevents unauthorized modification or tampering with data.
- Non-repudiation: Guarantees that the sender of a message cannot deny sending it.
However, encryption also has limitations:
- Computational cost: Encryption and decryption processes can be computationally intensive, especially for large datasets.
- Key management: Proper key management is crucial to prevent unauthorized access to encrypted data.
2. Data Transformation Process

Encryption involves converting recognizable data (plaintext) into an unrecognizable format (ciphertext) through the use of encryption algorithms. These algorithms employ mathematical operations to scramble the plaintext, making it unintelligible without the corresponding decryption key.
The encryption process can be represented as follows:
| Plaintext | Encryption Algorithm | Ciphertext |
|---|---|---|
| Hello World | AES-256 | U2FsdGVkX1+FMdJqQugx0A== |
The decryption process reverses this transformation, converting the ciphertext back into plaintext using the same encryption algorithm and decryption key.
3. Key Management and Security
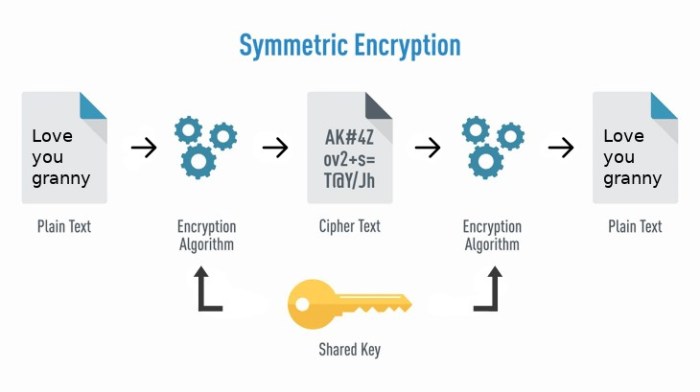
Key management is a critical aspect of encryption systems. Encryption keys are used to encrypt and decrypt data, and their security is paramount to protecting encrypted information.
Key management techniques include:
- Symmetric encryption: Uses the same key for both encryption and decryption.
- Asymmetric encryption: Employs a pair of keys – a public key for encryption and a private key for decryption.
Secure key storage and distribution practices are essential to prevent unauthorized access to encryption keys:
- Hardware security modules (HSMs)
- Key management systems (KMSs)
- Multi-factor authentication
4. Encryption Standards and Protocols
Industry-standard encryption algorithms and protocols ensure interoperability and security across different systems and applications.
Common encryption algorithms include:
- Advanced Encryption Standard (AES)
- Triple DES (3DES)
- RSA
Encryption protocols provide a framework for secure communication and data exchange:
- Secure Sockets Layer (SSL)/Transport Layer Security (TLS)
- Pretty Good Privacy (PGP)
- Secure Shell (SSH)
Encryption standards and protocols evolve over time to address emerging threats and advancements in computing technology.
5. Applications of Encryption
Encryption finds diverse applications across industries, including:
- Data storage: Encrypting sensitive data at rest in databases, cloud storage, and file systems.
- Communication: Securing email, instant messaging, and other communication channels.
- Financial transactions: Protecting financial data, such as credit card numbers and bank account information.
- Healthcare: Encrypting patient records and medical images to ensure privacy and confidentiality.
- Government and military: Safeguarding classified information and communication.
6. Ethical Considerations: Encryption Converts Unrecognizable Data Into Recognizable Data.
Encryption raises ethical considerations regarding data privacy, security, and surveillance.
Benefits of encryption for privacy include:
- Protection against data breaches and unauthorized access.
- Empowerment of individuals to control their own data.
Risks of encryption for security include:
- Potential misuse by criminals to conceal illegal activities.
- Challenges for law enforcement and intelligence agencies in accessing encrypted data for legitimate purposes.
Ethical considerations in encryption usage require careful balancing of these benefits and risks.
Essential Questionnaire
What is the purpose of encryption?
Encryption serves to protect sensitive data by making it unreadable to unauthorized individuals.
How does encryption work?
Encryption involves transforming data into an unreadable format using encryption algorithms and keys.
What are the benefits of using encryption?
Encryption offers numerous benefits, including data protection, privacy, and compliance with regulations.